Cyber-attacks are threatening businesses every day. It is crucial for business owners to understand how to protect their business from these attacks. Penetration testing is an important step in protecting your business. Penetration testing attempts to exploit vulnerabilities in systems, networks, human resources, or physical assets in order to stress test the effectiveness of the security controls.

Why Are Penetration Tests Performed?
Business owners can use penetration testing to evaluate the overall security of their IT infrastructure. Penetration tools are used to expose holes in a business’s security layer to allow security experts to address any possible vulnerabilities. These tests also serve as a mitigation technique to enable organizations to close any loopholes before threat actors get to them. Penetration testing reports assist developers in making fewer errors. In this article, we will discuss the different types of penetration testing.
The 3 Main Categories of Penetration Testing
These are three main types of penetration tests: black box, white box, and grey box.
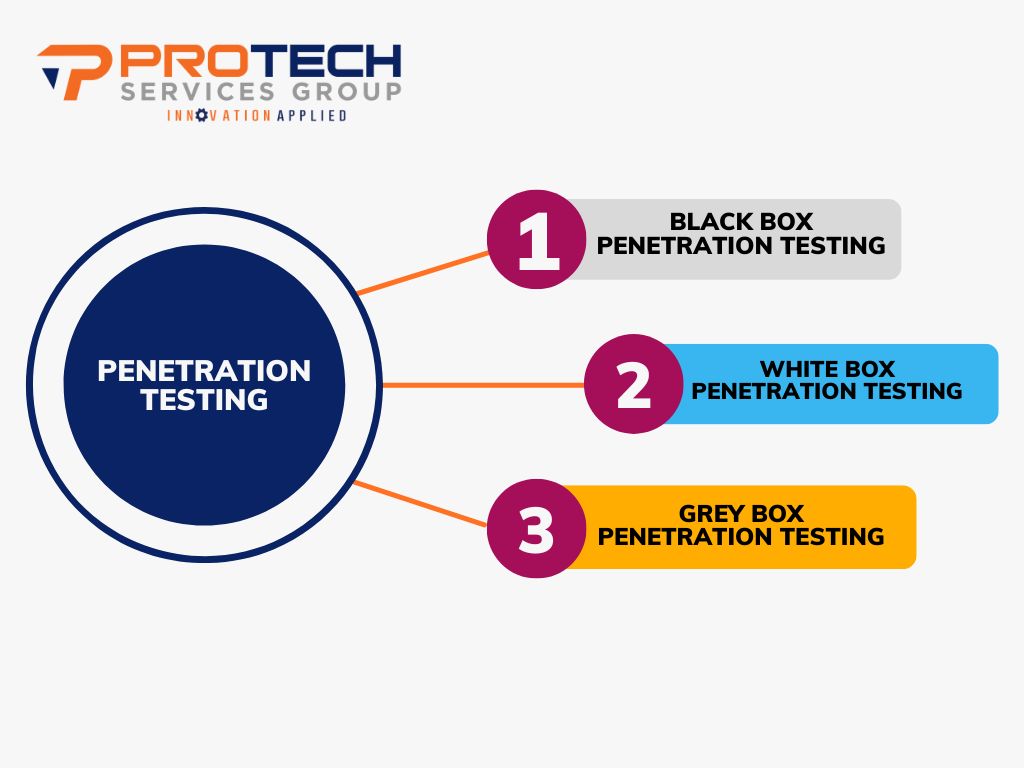
Black Box Penetration Testing
This type of security testing is where the tester has no prior knowledge of the system under test. In this test, the tester only has access to public information about the system. This type of security testing is often used to simulate a real-life attack from possible threats.
White Box Penetration Testing
In white box testing, the tester should have a complete knowledge of the system that’s under test. In this security test, the tester usually has access to the source code, architecture, and design of the system. By using this type of testing, you can find any possible vulnerabilities that black box testing methods may not be able to find.
Grey Box Penetration Testing
Grey box testing is used when the tester has partial knowledge of the system under test. In this test, the tester usually has access to some but not all of the information that would be available in the white box test. This type of security test is often used to find any vulnerabilities that may be difficult to find using black box or white box testing methods.
Types of Penetration Testing
There are many different types of penetration testing methods that can be performed. Each one has its own goals and objectives. Here are some of the common types of penetration testing methods:
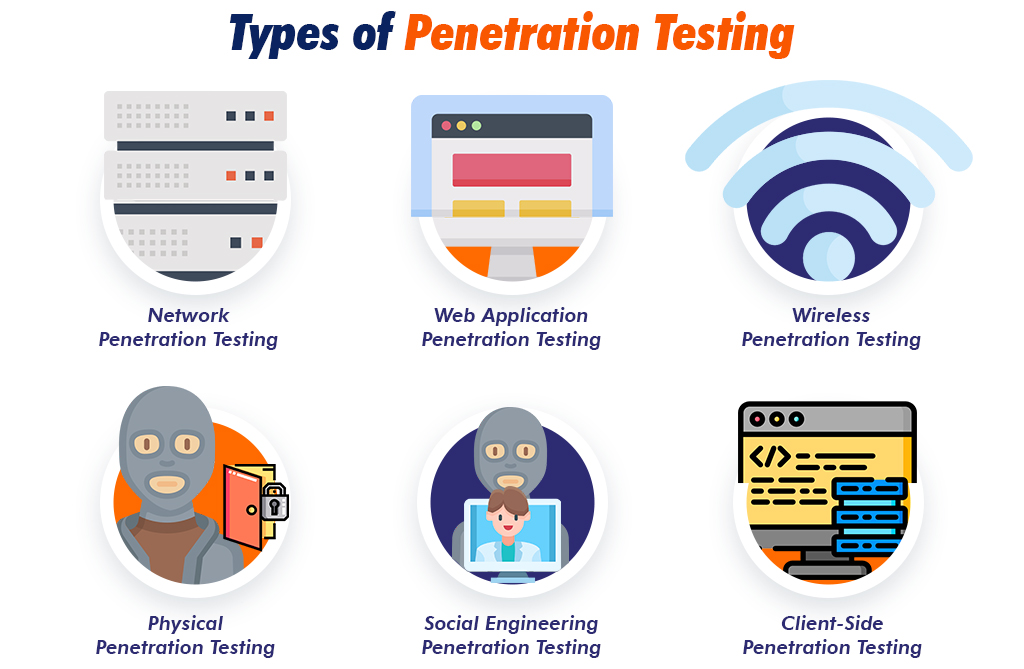
- Network Penetration Testing
This type of testing finds and exploits any exposed vulnerabilities in network infrastructure such as servers, firewalls, and switches. This testing can help protect your business from network-based attacks.
- Web Application Penetration Testing
This type of testing helps to find vulnerabilities in web-based applications. This testing of web applications can help to identify security vulnerabilities in databases, source code, and backend networks of web-based applications. It also helps to prioritize the vulnerabilities and provide solutions to mitigate them.
- Wireless Penetration Testing
This type of testing is used to identify risks that are associated with wireless networks and evaluate weaknesses. The strategy in this type of test is to find vulnerabilities that could be exploited by an attacker to gain access to the network.
- Physical Penetration Testing
This type of testing helps to secure an organization’s physical assets from potential threats. If a potential threat actor has physical access to a server, they can potentially compromise the entire network. In physical penetration testing, it finds weaknesses in physical controls such as locks, doors, cameras, or sensors, and allows the organization to remediate any defects.
- Social Engineering Penetration Testing
This type of testing, focuses the people and processes in the organization and the security vulnerabilities associated with them. This test is performed by ethical hackers who attempt social engineering attacks that are commonly experienced in the workplace. The main goal is to identify individuals, groups, or processes that are vulnerable and develop pathways for improving security awareness.
- Client-Side Penetration Testing
This type of testing helps to uncover security vulnerabilities in software running on client computers. Many attackers often compromise client-side software in order to gain access to the company infrastructure.
Conclusion
These security tests help to provide valuable information that your business can use to help strengthen security policies and mitigate any previously undiscovered risks. Protech’s mission is to create a layered security approach that helps to mitigate any risks and keep users informed. Our security approach is designed to work with a variety of services and tools to create an overall cybersecurity plan to protect you from potential threats and prepare you for an inevitable attack.